I’m running a website that is getting a lot of bot traffic and found Cloudflare free rule tier to be a bit limiting. (5 custom rules with length limits)
Ive got subnets for major VPS providers to block and will run analysis against my traffic to build on these lists.
What do others do?
I’m contemplating my Cloudflared tunnel into Crowdsec to my app.
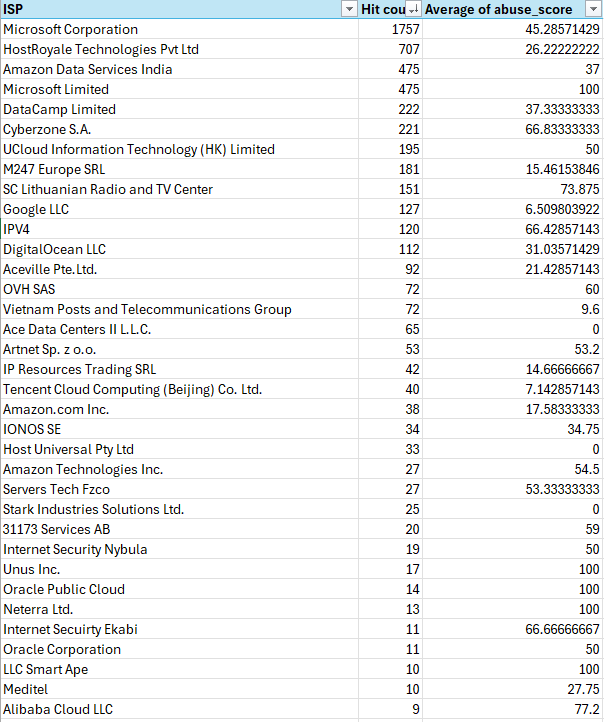
Edit: Adding in image of my analysis of the IPs scanning for vulnerabilities.
FYI, IP access rules don’t count towards the 5 custom rules limit, but the more generous 50k limit.
With fail2ban, you can setup IP access rules via the cftoken-action quite easily.
Security --> WAF --> Tools to access the IP rules in the dashboard. https://developers.cloudflare.com/waf/tools/ip-access-rules/
I have more than 50k but even that page doesn’t recommend it.
Top of that page
Recommendation: Use WAF custom rules instead
Cloudflare recommends that you create WAF custom rules instead of IP Access rules to perform IP-based or geography-based blocking (geoblocking):
- For IP-based blocking, use an IP list in the custom rule expression.
On the fail2ban front, can I run my traffic through a f2b container and out into my app?
WAF custom rules are more flexible, of course, and from a business perspective, I can understand why they would recommend that option instead.
I currently filter on an nginx access log file among other filters (sshd, bot-search, bad-requests) and let fail2ban execute the ban/unban action itself.
From a quick search, it should be possible to handle bans/unbans externally, if that’s what you’re after.
No I think f2b handling it would be totally fine for me. Kids got in the way with digging around too much but will try this week.
https://github.com/fail2ban/fail2ban
You can set
dbpurgeageto30dand pretty much just run it–or you can setupjail.confwith abantime.factor. Its appeal is that you basically can download it, enable it, and it just works for you. It depends on your environment, though. If you have incoming authorized requests from other services it might be a pain to configure, but I’ve never used anything easier to protect you from bad actors.I’ve used it on a machine before but given I am using a cloudflared container for ingress, can I route my traffic through a f2b container to the app? This might be ideal from a co fig perspective.
LLMs say yes but I’ll need to play around.
Yes, you just have to enable the built-in plugin for cloudflared: https://github.com/fail2ban/fail2ban/blob/master/config/action.d/cloudflare.conf
Ahhhmazing, I’ll set this up tonight. Really appreciate the help.
fail2ban isn’t a WAF?
fail2ban can be configured in just about any way you want. There’s no reason to say that fail2ban “isn’t” a WAF simply because it wasn’t designed that way. It’s kinda moot when it can be configured that way.
Give openappsec a try. It’s not entirely Open Source, howerver you don’t need to share anything with the company behind it (Check Point), and the solution “Just works” most of the time (fail2ban support included) without the hassle of adjusting a multitude of rules thanks to the use of AI. Just install and forget about it. I only had to create one custom rule, so the WAF would allow the upload of big files into my Nextcloud server. Keep in mind I only expose a couple of my own services to the Internet, that only me and couple of friends of mine will use, so I doubt I can be very representative here.
Wafs don’t make you safer but create unnecessary attack surface. Just keep your machine and services up to date.
You will need to explain a bit further this statement to mild knowledged internet stranger…
Because the point of waf is exactly about reducing the exposed surface…
Attack surface is made of the amount of code that is running when an attacker speaks to your machine. Imagine a freshly installed GNU/Linux distro with no services. The attack surface is minimal. All packages sent to your machine will only ever be touched by relatively limited parts of the linux TCP/IP stack and NIC driver. If you now run a web server, the package coes through the NIC driver, TCP/IP stack and web server. The surface is increased. Each of these parts of your machine’s code could have bugs. The more code your attacker’s packet runs through, the more opportunity to make your machine do things you don’t like.
If you want your machine to do what you like but not what random attackers like, it is therefore mandatory to have the least amount of attack surface, not adding code in contact with your attacker like a WAF or “antivirus”. Both these kind of softwares will inspect the packages coming in an take decisions (potentially bad ones) based on the content.
WAFs will mostly not help you since on a well configured and patched system, little known bugs are exposed. They might help you occasionally but usually patching the system is more effective. Of you want this to happen automatically, it’s entirely possible. Most os’s allow automatic unattended upgrades.
I’m trying to block the most likely attack vectors which is definitely VPS providers at this point in time. I just figure if I am blocking subnets plus additionals I identify it will force them out of these vectors to attack in ways I might be able to report better abuse.
Here check out my analysis.

Just don’t run broken software. The attackers will not be able to exploit you then. If they have zero day exploits, the WAF will most of the time not save you since they are often pretty easy to circumvent. WAFs are only effective against old and shitty exploits that should be patched anyways since ages.
I’d rather not have them probing my website at all. I’m not Facebook, my data is not unlimited and free.
Welcome to the internet. You will be probed. Just as your immune system, or rather your body, is being probed.



